A source of computer tips and secrets for friends, neighbors, and family of Duane Leet. Noone reading this blog is tracked and no information is associated with anyone.
Tuesday, April 25, 2017
Check Your Router!
Ask Leo! came through again. He linked to an article on router security that is a must read for my class. The article is: https://www.wordfence.com/blog/2017/04/home-routers-attacking-wordpress/. The article talks about Wordpress, which is a website implementation platform that is usually used for blogs and websites that look like blogs. As Leo points out, there's a link in the article that checks your router for a vulnerability with respect to bot insertion. By the way, the weakness described here is different than not changing your router's default password.
Saturday, April 22, 2017
Thursday, April 20, 2017
McAfee comments- especially for readers who were using AT&T Security and have moved on
AT&T offered a free security suite that was actually McAfee. I used that suite on my computers and found it worked fine. (I run Malwarebytes every now and then.) I was on the AT&T DSL Internet plan. I recently switched to a cable company. The AT&T security suite license terminated. So, what to do? I could click on the button McAfee provided to get a new subscription to the same service but, even with a "discount," the cost was not what I wanted.
So, I went to Amazon and typed in antivirus. I found among the results McAfee Antivirus Plus. That seemed to have all the features I wanted. Some of the higher function options, such as McAfee Total Protection, included services I don't need because I like Malwarebytes and CCleaner for those functions. Surprisingly, or NOT, Amazon offers a 14 license package of Antivirus Plus for $9.99. (I just looked again and the comparable offer today is 10 licenses for $9.99. I guess features vary from day to day.) Anyway, that's a good deal. This license package will cover my computers, tablets, and smartphones. I use Lookout on my Smartphone, but there are others in the household that can use a license as well.
So, I went to Amazon and typed in antivirus. I found among the results McAfee Antivirus Plus. That seemed to have all the features I wanted. Some of the higher function options, such as McAfee Total Protection, included services I don't need because I like Malwarebytes and CCleaner for those functions. Surprisingly, or NOT, Amazon offers a 14 license package of Antivirus Plus for $9.99. (I just looked again and the comparable offer today is 10 licenses for $9.99. I guess features vary from day to day.) Anyway, that's a good deal. This license package will cover my computers, tablets, and smartphones. I use Lookout on my Smartphone, but there are others in the household that can use a license as well.
Tuesday, April 18, 2017
Does Microsoft Edge Have a Way to Force https natively or by using an extension like https Everywhere?
This is an interesting question and, in my experience, demonstrates that Microsoft browsers are technically inferior to Chrome, Firefox, Opera, etc. The short answer appears to be, based on my search of the internet, that there is no way to enforce https where it is available. That feature appears to be TBD. The other browsers are supported by https Everywhere, which does the job.
If you know different, or you know of an extension that works with Edge, please comment below.
If you know different, or you know of an extension that works with Edge, please comment below.
March Breach Report by Lookout: 1.4B email addresses and personal info in 1 data breach
March was biggest month for compromised data yet with 1.4B exposed email addresses http://blog.lookout.com/blog/2017/04/07/breach-report-march-2017/
April 7, 2017
By Lookout
With over 1.45 billion compromised accounts, emails, social security numbers, dates of birth, and other data types, March was the biggest month for exposed data this year. Seventeen companies reported data breaches in March, totaling 1,449,373,000 breached accounts.
Major companies, including Saks Fifth Avenue, Coupa, and McDonald’s (Canada), experienced data loss.
However, according to email marketing organization River City Media’s public reports, the organization took the biggest hit with 1.4 billion exposed email addresses. That’s over 96% of the total breached accounts for the month. River City Media’s case highlights a very important point all individuals should know about data loss in today’s world: while any exposed data could spell trouble for the individual to whom it belonged, not all data loss or exposure is due to a malicious attack.
Sometimes companies make mistakes
There are a number of ways in which data is exposed that do not involve a nefarious actor breaking into a company’s systems and leaving with sensitive information. Sometimes companies themselves have security vulnerabilities, misconfigured servers, or other problems that leave data open and unprotected. In the case of River City Media, the company reported that the email addresses were stored in a database that was improperly secured, thereby exposing the data for anyone to access. Because these issues can go unnoticed for an unknown amount of time, the company may not know if anyone accessed that data during that period of time. Either way, a company will likely send an alert out to its customers.
Sometimes employees make mistakes
Another way companies might experience a non-malicious data breach is if an employee accidentally exposes the data. For example, last month a Boeing employee accidentally emailed a spreadsheet to his spouse that contained sensitive personal information of 36,000 Boeing employees. Boeing reported this as a data breach because, while non-malicious, it still exposed confidential data. It doesn’t matter how it’s exposed, breached data is still a problem Whether an attacker steals the information or it’s leaked through other means, stolen data could still spell trouble for the impacted individual who used that service.
Summary
In March, the top types of compromised data were (in order):
April 7, 2017
By Lookout
With over 1.45 billion compromised accounts, emails, social security numbers, dates of birth, and other data types, March was the biggest month for exposed data this year. Seventeen companies reported data breaches in March, totaling 1,449,373,000 breached accounts.
Major companies, including Saks Fifth Avenue, Coupa, and McDonald’s (Canada), experienced data loss.
However, according to email marketing organization River City Media’s public reports, the organization took the biggest hit with 1.4 billion exposed email addresses. That’s over 96% of the total breached accounts for the month. River City Media’s case highlights a very important point all individuals should know about data loss in today’s world: while any exposed data could spell trouble for the individual to whom it belonged, not all data loss or exposure is due to a malicious attack.
Sometimes companies make mistakes
There are a number of ways in which data is exposed that do not involve a nefarious actor breaking into a company’s systems and leaving with sensitive information. Sometimes companies themselves have security vulnerabilities, misconfigured servers, or other problems that leave data open and unprotected. In the case of River City Media, the company reported that the email addresses were stored in a database that was improperly secured, thereby exposing the data for anyone to access. Because these issues can go unnoticed for an unknown amount of time, the company may not know if anyone accessed that data during that period of time. Either way, a company will likely send an alert out to its customers.
Sometimes employees make mistakes
Another way companies might experience a non-malicious data breach is if an employee accidentally exposes the data. For example, last month a Boeing employee accidentally emailed a spreadsheet to his spouse that contained sensitive personal information of 36,000 Boeing employees. Boeing reported this as a data breach because, while non-malicious, it still exposed confidential data. It doesn’t matter how it’s exposed, breached data is still a problem Whether an attacker steals the information or it’s leaked through other means, stolen data could still spell trouble for the impacted individual who used that service.
Summary
In March, the top types of compromised data were (in order):
- Individuals’ names
- Dates of birth
- Email addresses
- Social security numbers
Monday, April 17, 2017
Dun and Bradstreet 33.6M records exposed
This is from http://www.ecommercetimes.com/story/84387.html. I can't tell from the one story what the date range for the data is. Note the links at the end go to a way to test employees family or customers on their vulnerability to phishing emails.
Dun and Bradstreet Marketing Breached
Dun & Bradstreet Marketing experienced a breach to one of their databases. The database was 52 GB, which included 33.6 million files. According to eCommerce Times, the database belonged to NetProspex.
The information exposed is basic contact information, very similar to what you may find on a business card — individual’s name, job title and contact information. eCommerce Times reported the primary threat with this breach is identity theft. However, I would have to disagree. Hackers now have over 30 million email addresses that they can use for phishing scams. Considering 93% of all phishing attacks include ransomware, this should be the highest concern.
The database that was breached included contact information for individuals working in various entities including Department of Defense, U.S. Air Force, U.S. Army, U.S. Postal Service, CVS Health Corporation, Wells Fargo and Wal-Mart, to name a few.
Prevention
It is encouraged, each entity impacted by this breach, conduct a cyber security training with all of their employees. Too often, it is believed phishing scams will be filtered to the spam folder. This is not always the case. Hackers are typically rather smart, and make the emails look legitimate. They do so by editing the “from” address to someone the recipient will know. This may be their boss, co-worker, or even a well-known business such as Amazon.
KnowBe4 offers a phishing simulation email that employers can send to their employees to see how vulnerable their company may be to such attack.
Case Study on finding other people's information on the internet: James Comey
The following is a blog post that shows how relatively "easy" it is for the younger generations to trace identities. The blog is from http://gizmodo.com/this-is-almost-certainly-james-comey-s-twitter-account-1793843641. You can go there for all the pictures and videos, which are deleted from this copy. (Content alert: Be careful clicking on things on that page. Better to just look at it and not play the movies, click links, etc.) It is also interesting to see the twitter post subject.
This Is Almost Certainly James Comey’s Twitter Account
 gizmodo.com
gizmodo.com
 Digital security and its discontents—from Hillary Clinton’s emails to ransomware to Tor hacks—is in many ways one of the chief concerns of the contemporary FBI. So it makes sense that the bureau’s director, James Comey, would dip his toe into the digital torrent with a Twitter account. It also makes sense, given Comey’s high profile, that he would want that Twitter account to be a secret from the world, lest his follows and favs be scrubbed for clues about what the feds are up to. What is somewhat surprising, however, is that it only took me about four hours of sleuthing to find Comey’s account, which is not protected.
Digital security and its discontents—from Hillary Clinton’s emails to ransomware to Tor hacks—is in many ways one of the chief concerns of the contemporary FBI. So it makes sense that the bureau’s director, James Comey, would dip his toe into the digital torrent with a Twitter account. It also makes sense, given Comey’s high profile, that he would want that Twitter account to be a secret from the world, lest his follows and favs be scrubbed for clues about what the feds are up to. What is somewhat surprising, however, is that it only took me about four hours of sleuthing to find Comey’s account, which is not protected.
Last night, at the Intelligence and National Security Alliance leadership dinner, Comey let slip that he has both a secret Twitter and an Instagram account in the course of relating a quick anecdote about one of his daughters.
Who am I to say no to a challenge?
As far as finding Comey’s Twitter goes, the only hint he offered was the fact that he has “to be on Twitter now,” meaning that the account would likely be relatively new. Regarding his Instagram identity, though, Comey gave us quite a bit more to work with:
... I care deeply about privacy, treasure it. I have an Instagram account with nine followers. Nobody is getting in. They’re all immediate relatives and one daughter’s serious boyfriend. I let them in because they’re serious enough. I don’t want anybody looking at my photos. I treasure my privacy and security on the internet. My job is public safety.
Both a noble sentiment and an extremely helpful clue for tracking down the FBI director’s social media accounts. Because, presumably, if we can find the Instagram accounts belonging to James Comey’s family, we can also find James Comey.
Unfortunately, Instagram isn’t exactly conducive to custom searching, and there was no way any of his five children or his wife would be using their full names. Twitter, however, gives us a little more leverage.
After some trial and error, I found that his 22-year-old son, Brien Comey, seemed to have the largest online presence as a basketball star at Kenyon College.
It wasn’t easy to find Brien Comey on Twitter, though, because his first name is also the middle name of his father, who more people than you might think call “James Brien Comey” on Twitter.
After a few frustrated attempts, I tried the following Twitter search on a whim:
This would bring up any mentions of the younger Comey while leaving out any references to his father.
That led me to this tweet from the Twitter account of the Kenyon College basketball team, on which the younger Comey played as an undergraduate. It showed Comey teaching basketball to some schoolkids, and @-mentioned the now-dead Twitter account “@twittafuzz.” That account, if you search through its mentions, appears to have been previously owned by Brien Comey—if you believe the folks on Twitter congratulating @twittafuzz for his dad’s ascension to the head of the FBI.
The trail ultimately led me here:
{picture}
Click through to the linked photo, and you’ll find that a well-wisher has left a comment in which none other than Brien Comey is tagged. Now, our FBI Director has trained his son well. His Instagram account is locked down. Instagram itself, however, offers a little loophole that is terrible for user privacy but wonderfully helpful for our purposes today.
Using the fake Instagram account I keep for the sole purpose of tracking Donald Trump Jr. and Newt Gingrich, I requested access to Brien Comey’s account. As soon as I did, this popped up: (picture)
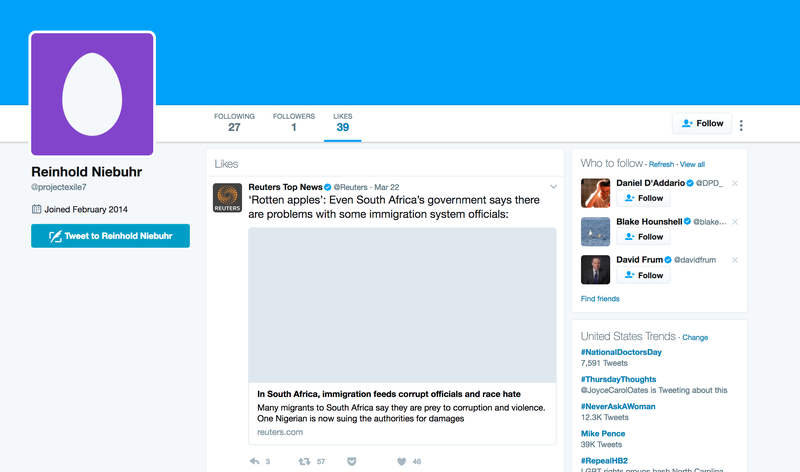
The suggestions were algorithmically selected based on the account I requested to follow, a significant number of which bore the last name “Comey” (Patrice is his wife). Among the various Comeys, only two of the suggested accounts lacked both real names and profile photos. And only one of these had anywhere near the “nine followers” that James Comey claimed to have. That account was reinholdniebuhr.
I still wasn’t sure that this was, in fact, James Comey. But a quick Google search turned up this article on Comey’s time at the College of William and Mary, and my doubts were assuaged:
By senior year, Comey was a double major in religion and chemistry, writing a senior thesis on theologian Reinhold Niebuhr and televangelist Jerry Falwell and on his way to the University of Chicago Law School
With Instagram solved, it was time to move back to Twitter. Though there is an @ReinholdNiebuhr, based on the tweets alone I was pretty sure that he was not our guy.
But fortunately for us, there are only seven accounts on Twitter currently using some variation of “Reinhold Niebuhr” as a user name.
And only one that seemed to be operating in stealth: @projectexile7.
But how to be sure? There is only one person currently following the account: Benjamin Wittes of Lawfare. Wittes is no Twitter neophyte. He is an active user with more than 25,000 followers, and he only follows 1,178 accounts—meaning he is not a subscriber to the “followback” philosophy. If he is following a random egg—and is the only account following it—there is probably a reason.
That reason could be the fact that, as Wittes wrote here, he is a personal friend of James Comey. (We’ve reached out to Wittes for comment but have yet to hear back.)
Project Exile happens to be a federal program that James Comey helped develop when he was a U.S. attorney living in Richmond. And then, of course, there are the follows.
ProjectExile7 follows 27 other accounts, the majority of which are either reporters, news outlets, or official government and law enforcement accounts. The New York Times’ Adam Goldman and David Sanger and the Washington Post’s Ellen Nakashima and David Ignatius, all of whom have been aggressively covering the FBI investigation into Trump’s contacts with Russian agents, made the list, as did Wittes and former Bush Administration colleague Jack Goldsmith. Donald Trump is on there, too, but @projectexile7 seems to have begun following him relatively recently (its first follow was @nytimes).
There are two outliers: William and Mary News (where Comey attended undergrad) and our colleagues at The Onion (everyone deserves to have fun):
And of the 39 total tweets the account has liked thus far, eight refer directly to the FBI or James Comey himself: (picture)
One deals with an active FBI investigation: (picture)
And four refer to the Trump administration in general: (picture)
Of course, none of this is definitive proof @projectexile7 is FBI Director James Comey, but it would take a nearly impossible confluence of coincidences for it to be anyone else. Take what you will from the fact that the director of the FBI appears to have liked a tweet from the New York Times about Mike Flynn and Jared Kushner meeting a Russian envoy in December.
We’ve reached out to the FBI for comment, and will update if and when we hear back.
The FBI has officially weighed in:
Hello,
We don’t have any comment.
Thank you.
FBI National Press Office
This story was produced by the Special Projects Desk of Gizmodo Media Group.
This Is Almost Certainly James Comey’s Twitter Account
 Digital security and its discontents—from Hillary Clinton’s emails to ransomware to Tor hacks—is in many ways one of the chief concerns of the contemporary FBI. So it makes sense that the bureau’s director, James Comey, would dip his toe into the digital torrent with a Twitter account. It also makes sense, given Comey’s high profile, that he would want that Twitter account to be a secret from the world, lest his follows and favs be scrubbed for clues about what the feds are up to. What is somewhat surprising, however, is that it only took me about four hours of sleuthing to find Comey’s account, which is not protected.
Digital security and its discontents—from Hillary Clinton’s emails to ransomware to Tor hacks—is in many ways one of the chief concerns of the contemporary FBI. So it makes sense that the bureau’s director, James Comey, would dip his toe into the digital torrent with a Twitter account. It also makes sense, given Comey’s high profile, that he would want that Twitter account to be a secret from the world, lest his follows and favs be scrubbed for clues about what the feds are up to. What is somewhat surprising, however, is that it only took me about four hours of sleuthing to find Comey’s account, which is not protected.Who am I to say no to a challenge?
... I care deeply about privacy, treasure it. I have an Instagram account with nine followers. Nobody is getting in. They’re all immediate relatives and one daughter’s serious boyfriend. I let them in because they’re serious enough. I don’t want anybody looking at my photos. I treasure my privacy and security on the internet. My job is public safety.
Both a noble sentiment and an extremely helpful clue for tracking down the FBI director’s social media accounts. Because, presumably, if we can find the Instagram accounts belonging to James Comey’s family, we can also find James Comey.
Unfortunately, Instagram isn’t exactly conducive to custom searching, and there was no way any of his five children or his wife would be using their full names. Twitter, however, gives us a little more leverage.
It wasn’t easy to find Brien Comey on Twitter, though, because his first name is also the middle name of his father, who more people than you might think call “James Brien Comey” on Twitter.
After a few frustrated attempts, I tried the following Twitter search on a whim:
This would bring up any mentions of the younger Comey while leaving out any references to his father.
That led me to this tweet from the Twitter account of the Kenyon College basketball team, on which the younger Comey played as an undergraduate. It showed Comey teaching basketball to some schoolkids, and @-mentioned the now-dead Twitter account “@twittafuzz.” That account, if you search through its mentions, appears to have been previously owned by Brien Comey—if you believe the folks on Twitter congratulating @twittafuzz for his dad’s ascension to the head of the FBI.
{picture}
Click through to the linked photo, and you’ll find that a well-wisher has left a comment in which none other than Brien Comey is tagged. Now, our FBI Director has trained his son well. His Instagram account is locked down. Instagram itself, however, offers a little loophole that is terrible for user privacy but wonderfully helpful for our purposes today.
The suggestions were algorithmically selected based on the account I requested to follow, a significant number of which bore the last name “Comey” (Patrice is his wife). Among the various Comeys, only two of the suggested accounts lacked both real names and profile photos. And only one of these had anywhere near the “nine followers” that James Comey claimed to have. That account was reinholdniebuhr.
I still wasn’t sure that this was, in fact, James Comey. But a quick Google search turned up this article on Comey’s time at the College of William and Mary, and my doubts were assuaged:
With Instagram solved, it was time to move back to Twitter. Though there is an @ReinholdNiebuhr, based on the tweets alone I was pretty sure that he was not our guy.
But fortunately for us, there are only seven accounts on Twitter currently using some variation of “Reinhold Niebuhr” as a user name.
And only one that seemed to be operating in stealth: @projectexile7.
But how to be sure? There is only one person currently following the account: Benjamin Wittes of Lawfare. Wittes is no Twitter neophyte. He is an active user with more than 25,000 followers, and he only follows 1,178 accounts—meaning he is not a subscriber to the “followback” philosophy. If he is following a random egg—and is the only account following it—there is probably a reason.
Project Exile happens to be a federal program that James Comey helped develop when he was a U.S. attorney living in Richmond. And then, of course, there are the follows.
ProjectExile7 follows 27 other accounts, the majority of which are either reporters, news outlets, or official government and law enforcement accounts. The New York Times’ Adam Goldman and David Sanger and the Washington Post’s Ellen Nakashima and David Ignatius, all of whom have been aggressively covering the FBI investigation into Trump’s contacts with Russian agents, made the list, as did Wittes and former Bush Administration colleague Jack Goldsmith. Donald Trump is on there, too, but @projectexile7 seems to have begun following him relatively recently (its first follow was @nytimes).
And of the 39 total tweets the account has liked thus far, eight refer directly to the FBI or James Comey himself: (picture)
One deals with an active FBI investigation: (picture)
And four refer to the Trump administration in general: (picture)
Of course, none of this is definitive proof @projectexile7 is FBI Director James Comey, but it would take a nearly impossible confluence of coincidences for it to be anyone else. Take what you will from the fact that the director of the FBI appears to have liked a tweet from the New York Times about Mike Flynn and Jared Kushner meeting a Russian envoy in December.
We’ve reached out to the FBI for comment, and will update if and when we hear back.
The FBI has officially weighed in:
Hello,
We don’t have any comment.
Thank you.
FBI National Press Office
This story was produced by the Special Projects Desk of Gizmodo Media Group.
Sunday, April 9, 2017
Personal and Small Business Security- Lecture 2
It takes a lot of time to convert a Powerpoint slide to a form that works on a blog. Rather than do that, my practice now will be to create a PDF document and share on this blog through a link. So, here is Lecture 2.
Saturday, April 8, 2017
South Carolina Computer Crime Law
Computer Crime Laws in South Carolina
from https://statelaw.findlaw.com
The chart below highlights some of South Carolina’s computer crime statutes.
Code Section
|
South Carolina Code of Laws 16-16-10, et seq.: Computer Crime Act
|
What Is Prohibited
|
Directly or indirectly accessing or causing to be accessed a computer, computer system, or computer network for the purpose of:
Altering, damaging, destroying, or modifying a computer, computer system, computer network, computer software, computer program, or data contained in that computer, computer system, computer program, or computer network or introduce a computer contaminant into that computer, computer system, computer program, or computer network.
|
Mental State Required for Prosecution
|
Willfully, knowingly, maliciously
|
Misdemeanor Computer Crimes
|
Computer crime in the second degree, class A misdemeanor; Computer crime in the third degree, class B misdemeanor
|
Felony Computer Crimes
|
Computer crime in the first degree, class E felony; second or subsequent convictions of computer crimes in the second degree, class F felony
|
Attempt Considered a Crime?
|
No
|
Civil Lawsuit Permitted?
|
No
|
Related Resources for South Carolina Computer Crimes Laws:
Contacts at state level:
(803) 896-7901
CAPTAIN SAMUEL C. REIGHLEY, JR.
(803) 896-8389
LIEUTENANT BRITT DOVE
(803) 896-7901
24 Hour ON-CALL
(803) 737-9000
My experience is that state contact is not worth much. If you have a real crime, contact your local county sheriff or, if you live in a city, your local police department to report the crime. Get a case number. Then, if money is involved, contact your financial institution and ask for the fraud or theft people, whatever they call themselves. They will want that case number to give you credit.
By the way, I find it remarkable that the state gov site is not secured (http vs https)
Wednesday, April 5, 2017
iso file to USB bootable flash drive
Those taking my security class have a need to know about obtaining .iso files and writing those files, in bootable form, to a USB drive. (It used to be that the target of choice was a DVD, but many computers are not equipped with a DVD drive. If you have a DVD drive and just want to create an DVD from the .iso, then I love ImgBurn. It really works well, its default setup works most of the time, and the user has access to all the bells and whistle to customize the copy.)
I have put a guide to the different .iso to USB drive free applications on a PDF file and you can find it here.
I'm trying some of the options to determine which one works best to produce a live bootable drive for a .iso file.
I have put a guide to the different .iso to USB drive free applications on a PDF file and you can find it here.
I'm trying some of the options to determine which one works best to produce a live bootable drive for a .iso file.
Tuesday, April 4, 2017
What's the difference between https and VPN? Don't they do the same thing?
You know that HTTPS (Secure HTTP) and VPN (Virtual Private Network) are a more secure way to browse the web but what exactly happens behind the scenes when you use either of these options? Why do you need to use a VPN when you have already turned on HTTPS?
The Privacy Team at Google has recently added a couple of short and useful videos to YouTube that try to explain technical jargon like HTTPS, VPN, WPA (for secure Wi-Fi) in simple English and why these are important. Take a look: https://youtu.be/_p-LNLv49Ug HTTPS in simple english. https://youtu.be/B41vCC4KLkY VPN in Simple English
The basic idea is that you encrypt traffic between your computer and the web server so that eavesdroppers cannot see any of that information. HTTPS will only encrypt traffic between your browser and a particular website while VPN will encrypt all traffic between your computer and the Internet. So that is the answer to the Post Subject: VPN encrypts everything between you and the VPN server, whether you use https or not. https encrypts only between you and the target server named in the url.
Neither one does anything about maintaining encryption at the other end. That is up to the receiving server.
If you add the extension HTTPS Everywhere to your browser, then your browser will try to force https to every url. If it doesn't succeed, you will get a warning in the address bar.
Personally, unless you are communicating to a company server, I don't see any use for VPN except providing an IP address that is not your location IP address.
The Privacy Team at Google has recently added a couple of short and useful videos to YouTube that try to explain technical jargon like HTTPS, VPN, WPA (for secure Wi-Fi) in simple English and why these are important. Take a look: https://youtu.be/_p-LNLv49Ug HTTPS in simple english. https://youtu.be/B41vCC4KLkY VPN in Simple English
The basic idea is that you encrypt traffic between your computer and the web server so that eavesdroppers cannot see any of that information. HTTPS will only encrypt traffic between your browser and a particular website while VPN will encrypt all traffic between your computer and the Internet. So that is the answer to the Post Subject: VPN encrypts everything between you and the VPN server, whether you use https or not. https encrypts only between you and the target server named in the url.
Neither one does anything about maintaining encryption at the other end. That is up to the receiving server.
If you add the extension HTTPS Everywhere to your browser, then your browser will try to force https to every url. If it doesn't succeed, you will get a warning in the address bar.
Personally, unless you are communicating to a company server, I don't see any use for VPN except providing an IP address that is not your location IP address.
Monday, April 3, 2017
Lastpass Vulnerability and Fix
{Update: I have added a video by "Ask Leo" on this topic to the video playlist you can access through the Youtube widget on the right side of this blog. He specifically addresses the issue: "Is it safe."}
A vulnerability in Lastpass was discovered and "fixed" this past weekend. I will discuss this in class. The extension/plugin version with the fix is 4.1.45. In Chrome, you can find the version of the extension in Settings. Click Extensions in the left navigator bar and scroll down to find Lastpass. The version is listed next to the name.
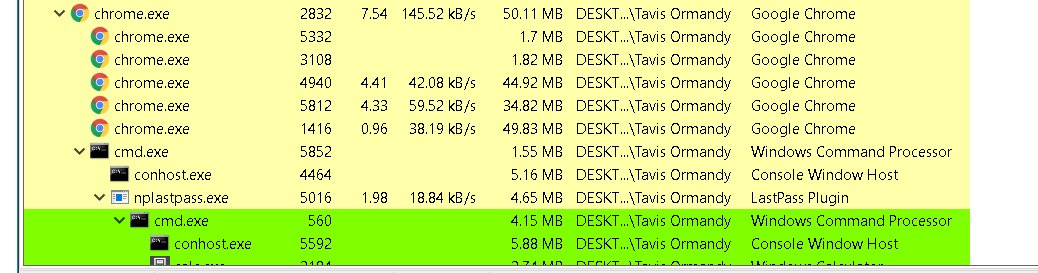
A vulnerability in Lastpass was discovered and "fixed" this past weekend. I will discuss this in class. The extension/plugin version with the fix is 4.1.45. In Chrome, you can find the version of the extension in Settings. Click Extensions in the left navigator bar and scroll down to find Lastpass. The version is listed next to the name.
Original Tweet
The original tweet was posted on March 25 (https://twitter.com/taviso/status/845717082717114368). Ah-ha, I had an epiphany in the shower this morning and realized how to get codeexec in LastPass 4.1.43. Full report and exploit on the way.
Publication in Press:
From: https://arstechnica.com/security/2017/03/potent-lastpass-exploit-underscores-the-dark-side-of-password-managers/
Developers of the widely used LastPass password manager are scrambling to fix a serious vulnerability that makes it possible for malicious websites to steal user passcodes and in some cases execute malicious code on computers running the program.
The flaw, which affects the latest version of the LastPass browser extension, was briefly described on Saturday by Tavis Ormandy, a researcher with Google's Project Zero vulnerability reporting team. When people have the LastPass binary running, the vulnerability allows malicious websites to execute code of their choice. Even when the binary isn't present, the flaw can be exploited in a way that lets malicious sites steal passwords from the protected LastPass vault. Ormandy said he developed a proof-of-concept exploit and sent it to LastPass officials. Developers now have three months to patch the hole before Project Zero discloses technical details.
"It will take a long time to fix this properly," Ormandy said. "It's a major architectural problem. They have 90 days, no need to scramble!"
In a blog post published Monday, LastPass officials thanked Ormandy for alerting them to the bug and said a fix was on the way. In the meantime, they said LastPass users should protect themselves by entering stored passwords into websites using the LastPass vault as a launch pad for opening websites and entering passwords and enabling two-factor authentication on sites that offer it.
"This attack is unique and highly sophisticated," the blog post warned. "We don’t want to disclose anything specific about the vulnerability or our fix that could reveal anything to less sophisticated but nefarious parties. So you can expect a more detailed post mortem once this work is complete."
https://arstechnica.com/security/2017/03/potent-lastpass-exploit-underscores-the-dark-side-of-password-managers/ The vulnerability is the third one Ormandy has privately reported to LastPass this month. Last week, he described bare-bones details of two different flaws found in LastPass extensions for multiple browsers. LastPass developers quickly implemented changes on their server that made the flaws harder to exploit and released patches two days later.
The string of vulnerabilities underscores the tradeoff that comes from use of any password manager. Storing dozens, hundreds, or even thousands of passwords in a single place poses catastrophic risks should that resource be breached. Exploits become easier by convenience features that, for example, store encrypted password vaults in Internet-accessible locations or automatically paste passwords into websites. Ultimately, password managers likely make the average user safer because they make it possible to use long, complex, and unique passwords. And that protects people in the event that their password is exposed in website breaches, which are much more common than real-world password manager exploits.
Most users will be updated automatically. Please ensure you are running the latest version (4.1.44 or higher), which can always be downloaded at https://www.lastpass.com/.
Now that the issue is resolved, we want to provide a postmortem to our community on what the report entailed and how we are building a better, more secure LastPass going forward. Please note, due to the nature of the vulnerability, this postmortem is highly technical.
Overview
This client-side vulnerability in the LastPass browser extensions was caused by the way LastPass behaves in “isolated worlds”. As noted in the report, “an isolated world is a JavaScript execution environment that shares the same DOM (Document Object Model) as other worlds, but things like variables and functions are not shared. Without isolated worlds, unprivileged pages could interfere with higher privileged scripts, and make them do whatever they want.” In the case of those running the binary version of the extension, which is less than 10% of LastPass users, it could have been manipulated to allow remote code execution (RCE) on the extension.
“Isolated worlds” and Trusted Pages
A major part of how LastPass works is content scripts. Content scripts are snippets of JavaScript that we inject into 3rd-party sites in order to capture login information and perform autofill. These are a major part of what makes LastPass so useful. In turn, the content script communicates with the rest of the extension to do the heavy lifting: decrypting saved sites, updating the vault, and so on. The rest of the extension is completely inaccessible to 3rd-party sites and should not be able to influence the content scripts.
The content scripts are ordinarily set apart from the rest of the site through the concept of “isolated worlds”. Isolated worlds means our content scripts can read the DOM contents of a 3rd party site, but not any internal JavaScript functions or variables. The reverse also applies: The 3rd party site cannot call any functions or access any variables in our content scripts. The separation is supposed to keep both sides safer from external manipulation.
In some cases, these variables can influence the logic of the content script. It is difficult to inject arbitrary values into JavaScript using this technique. But in a particularly clever move, the report demonstrated that arbitrary strings could be injected, and one of these was enough to trick the extension into thinking it was executing on lastpass.com. By doing so, an attacker could manipulate the LastPass extension into revealing the stored data of that user, and launch arbitrary executables in the case of the binary version.
Our assumption was that we could trust the global scope in which our content scripts run, and this proved not to be the case. Consequently, there were many locations in our JavaScript where it was possible for externally-supplied, global variables to override a default value.
Fixing the issue
Immediately after we received the full report, a cross-functional response team investigated and validated the findings. It was clear that addressing the issues would require a significant change to our browser extensions. This was not a simple patch, and required a thoughtful, thorough fix. Those changes then needed to be applied and tested across all affected extensions.
To fix, we addressed variable handling and added the Proxy object to the outer scope of the content script, acting as a “sandbox” to prevent externally-supplied window properties from being read within the content script. To further mitigate RCE, we put in place restrictions on the types of attachments that the extension can launch and limited the available extension APIs.
We worked directly with Google’s Project Zero to verify that our fixes were comprehensive. Once the fix was ready for all affected extensions, we were able to have them reviewed by all stores and pushed to users very quickly. We want to thank our partners at Apple, Google, Microsoft, Mozilla, Opera, Yandex and others who fast-tracked our extension review and release.
Looking ahead
We strongly urge other extension developers to look for this pattern in their code and ensure they are not vulnerable.
We’re in the business of password management; security is and always will be our top priority. We greatly appreciate the work of the security community who challenges our product and works with our teams to ensure we’re delivering a secure service for our users. As a market leader, we get the best of the best testing LastPass and in return our software and our customers benefit.
In an effort to maintain the highest level of security, we will continue to partner with white-hat security researchers and provide incentives to participate in our bug bounty program (https://bugcrowd.com/lastpass). Stay tuned for more to come on this.
Thank you,
The LastPass Team
Developers of the widely used LastPass password manager are scrambling to fix a serious vulnerability that makes it possible for malicious websites to steal user passcodes and in some cases execute malicious code on computers running the program.
The flaw, which affects the latest version of the LastPass browser extension, was briefly described on Saturday by Tavis Ormandy, a researcher with Google's Project Zero vulnerability reporting team. When people have the LastPass binary running, the vulnerability allows malicious websites to execute code of their choice. Even when the binary isn't present, the flaw can be exploited in a way that lets malicious sites steal passwords from the protected LastPass vault. Ormandy said he developed a proof-of-concept exploit and sent it to LastPass officials. Developers now have three months to patch the hole before Project Zero discloses technical details.
"It will take a long time to fix this properly," Ormandy said. "It's a major architectural problem. They have 90 days, no need to scramble!"
In a blog post published Monday, LastPass officials thanked Ormandy for alerting them to the bug and said a fix was on the way. In the meantime, they said LastPass users should protect themselves by entering stored passwords into websites using the LastPass vault as a launch pad for opening websites and entering passwords and enabling two-factor authentication on sites that offer it.
"This attack is unique and highly sophisticated," the blog post warned. "We don’t want to disclose anything specific about the vulnerability or our fix that could reveal anything to less sophisticated but nefarious parties. So you can expect a more detailed post mortem once this work is complete."
https://arstechnica.com/security/2017/03/potent-lastpass-exploit-underscores-the-dark-side-of-password-managers/ The vulnerability is the third one Ormandy has privately reported to LastPass this month. Last week, he described bare-bones details of two different flaws found in LastPass extensions for multiple browsers. LastPass developers quickly implemented changes on their server that made the flaws harder to exploit and released patches two days later.
The string of vulnerabilities underscores the tradeoff that comes from use of any password manager. Storing dozens, hundreds, or even thousands of passwords in a single place poses catastrophic risks should that resource be breached. Exploits become easier by convenience features that, for example, store encrypted password vaults in Internet-accessible locations or automatically paste passwords into websites. Ultimately, password managers likely make the average user safer because they make it possible to use long, complex, and unique passwords. And that protects people in the event that their password is exposed in website breaches, which are much more common than real-world password manager exploits.
Lastpass Response:
On Saturday, March 25th, security researcher Tavis Ormandy from Google’s Project Zero reported a security finding related to the LastPass browser extensions. In the last 24 hours, we’ve released an update which we believe fixes the reported vulnerability in all browsers and have verified this with Tavis himself.Most users will be updated automatically. Please ensure you are running the latest version (4.1.44 or higher), which can always be downloaded at https://www.lastpass.com/.
Now that the issue is resolved, we want to provide a postmortem to our community on what the report entailed and how we are building a better, more secure LastPass going forward. Please note, due to the nature of the vulnerability, this postmortem is highly technical.
Overview
- This was a client-side vulnerability in the LastPass browser extensions and could be exploited to steal data and manipulate the LastPass extension
- Exploiting required luring a user to a malicious website (through phishing, spearphishing, or other attack), or to a trusted website running malicious adware
- This requires a per-user attack that must be executed through the user’s local browser
- All extensions have now been updated with the fix and submitted to the extension stores
- Our mobile apps for Android, iOS, and Windows Phones were not affected
- All of your LastPass browser extensions should be updated to version 4.1.44 or higher
- Check the LastPass extension icon > More options > About LastPass for your version number
- Most users should be updated automatically, but the latest versions can always be downloaded at https://www.lastpass.com/
- Uninstalling is not required to download the updated version
This client-side vulnerability in the LastPass browser extensions was caused by the way LastPass behaves in “isolated worlds”. As noted in the report, “an isolated world is a JavaScript execution environment that shares the same DOM (Document Object Model) as other worlds, but things like variables and functions are not shared. Without isolated worlds, unprivileged pages could interfere with higher privileged scripts, and make them do whatever they want.” In the case of those running the binary version of the extension, which is less than 10% of LastPass users, it could have been manipulated to allow remote code execution (RCE) on the extension.
“Isolated worlds” and Trusted Pages
A major part of how LastPass works is content scripts. Content scripts are snippets of JavaScript that we inject into 3rd-party sites in order to capture login information and perform autofill. These are a major part of what makes LastPass so useful. In turn, the content script communicates with the rest of the extension to do the heavy lifting: decrypting saved sites, updating the vault, and so on. The rest of the extension is completely inaccessible to 3rd-party sites and should not be able to influence the content scripts.
The content scripts are ordinarily set apart from the rest of the site through the concept of “isolated worlds”. Isolated worlds means our content scripts can read the DOM contents of a 3rd party site, but not any internal JavaScript functions or variables. The reverse also applies: The 3rd party site cannot call any functions or access any variables in our content scripts. The separation is supposed to keep both sides safer from external manipulation.
In some cases, these variables can influence the logic of the content script. It is difficult to inject arbitrary values into JavaScript using this technique. But in a particularly clever move, the report demonstrated that arbitrary strings could be injected, and one of these was enough to trick the extension into thinking it was executing on lastpass.com. By doing so, an attacker could manipulate the LastPass extension into revealing the stored data of that user, and launch arbitrary executables in the case of the binary version.
Our assumption was that we could trust the global scope in which our content scripts run, and this proved not to be the case. Consequently, there were many locations in our JavaScript where it was possible for externally-supplied, global variables to override a default value.
Fixing the issue
Immediately after we received the full report, a cross-functional response team investigated and validated the findings. It was clear that addressing the issues would require a significant change to our browser extensions. This was not a simple patch, and required a thoughtful, thorough fix. Those changes then needed to be applied and tested across all affected extensions.
To fix, we addressed variable handling and added the Proxy object to the outer scope of the content script, acting as a “sandbox” to prevent externally-supplied window properties from being read within the content script. To further mitigate RCE, we put in place restrictions on the types of attachments that the extension can launch and limited the available extension APIs.
We worked directly with Google’s Project Zero to verify that our fixes were comprehensive. Once the fix was ready for all affected extensions, we were able to have them reviewed by all stores and pushed to users very quickly. We want to thank our partners at Apple, Google, Microsoft, Mozilla, Opera, Yandex and others who fast-tracked our extension review and release.
Looking ahead
We strongly urge other extension developers to look for this pattern in their code and ensure they are not vulnerable.
We’re in the business of password management; security is and always will be our top priority. We greatly appreciate the work of the security community who challenges our product and works with our teams to ensure we’re delivering a secure service for our users. As a market leader, we get the best of the best testing LastPass and in return our software and our customers benefit.
In an effort to maintain the highest level of security, we will continue to partner with white-hat security researchers and provide incentives to participate in our bug bounty program (https://bugcrowd.com/lastpass). Stay tuned for more to come on this.
Thank you,
The LastPass Team
Subscribe to:
Posts (Atom)