A source of computer tips and secrets for friends, neighbors, and family of Duane Leet. Noone reading this blog is tracked and no information is associated with anyone.
Tuesday, March 31, 2015
Wow! Google has a new contact manager that may enables sharing contact lists across organizations
This is the Google announcement: http://googlesystem.blogspot.com/2015/03/google-tests-new-contacts-interface.html. Copy and paste that into your address bar. It is an early March announcement, but I was just "automatically upgraded to the new version. It looks like, using the Google+ environment, you can create a "friends" group, which might be an organization you belong to (eg Barbershop, Church) and share the addresses between all that are in the group. It looks like Google is saying that your address list for your organization will be up-to-date for all people in your organization! Has anyone tried it?
Monday, March 30, 2015
Warning: Turbotax Fraud on Electronic Refunds- and Possible Coverup?
One of my acquaintances has had a terrible time with the electronic refund process of Turbotax. I thought I would describe what has happened as a warning to everyone that there is some built in slick bait and switch inside the Turbotax filing process and, in this case I am going to describe, perhaps some fraud from inside the Turbotax refund process (Important: The Turbotax refund process includes third party financial services, so Turbotax has plausible deniability if there is indeed something going on.)
If you are not familiar with what has gone on with Turbotax earlier, here is a summary I copied from Forbes (My story continues after this copy. Look for the horizontal line.):
If you are not familiar with what has gone on with Turbotax earlier, here is a summary I copied from Forbes (My story continues after this copy. Look for the horizontal line.):
TurboTax has resumed acceptance of electronically filed state tax returns after temporarily turning off service in all states on Thursday, February 5 after reports of suspicious activity.
The move to temporarily suspend service followed concerns in at least 18 states that taxpayer data had been compromised. The state of Minnesota actuallytook matters into its own hands, announcing that it would not accept returns transmitted by TurboTax.
As a result, Intuit INTU +1.52%, the company responsible for TurboTax, reached out to Palantir, a third party security expert, to investigate potentially fraudulent activities. The initial findings lead the company to believe that there was not a breach in TurboTax security but rather that data used to file fraudulent returns was obtained from other sources outside the tax preparation process. That data was used to file returns before honest taxpayers could file: when those taxpayers did log in, they found that someone else had already filed using their names and taxpayer information.
TurboTax is still working with state tax authorities to follow-up on the fraud allegations but believe resuming services at this time is appropriate. Brad Smith, Intuit president and chief executive officer, noted that the company is continuing to monitor the situation, saying, “We’ve identified specific patterns of behavior where fraud is more likely to occur. We’re working with the states to share that information and remedy the situation quickly. We will continue to engage them on an ongoing basis in an effort to stop fraud before it gets started.”
Intuit also implemented targeted security measures to combat the type of fraudulent tax activity that it is seeing. According to Julie Miller, Director, Public Relations & Social Media for Intuit, these additional steps include the implementation of Multi-Factor Authentication, a proven technology for protection against identity theft.
Meanwhile, taxpayers who were waiting to file their state returns can move forward. Taxpayers who filed state tax return using Intuit software during the hold don’t need to do anything further: any returns which were being held will be filed automatically as systems resume.
TurboTax stressed that the filing of federal income tax returns was not affected by the hold. The IRS confirmed that to be the case yesterday (see their statement).
Despite TurboTax’ insistence that the move was not system-specific, other tax preparation software companies reported that they were not seeing similar problems. H&R Block HRB -0.19%, which sits at #2 in popularity behind TurboTax in the tax software world, affirmatively stated that “[w]e have no indication this issue exists with H&R Block online state returns.” TaxACT issued a similar statement, stressing that “[w]e are not seeing similar activity in our proactive monitoring, and we will continue to partner with state agencies and the IRS to prevent fraud.”
So what makes one system vulnerable while others are not? And why target state and not federal returns?
So what makes one system vulnerable while others are not? And why target state and not federal returns?
It’s not exactly clear. But there may be some common denominators. Criminal tax fraud is big business – but it’s also a crime of opportunity. The more difficult it is to take advantage, the more likely the bad guys are going to pass. Remember that home alarm commercial that made the rounds a few years back? The one where the crooks saw the security company sign in the window and decided to move onto another house? It’s kind of like that.
That’s probably why criminals appeared to be targeting state returns and not federal returns. The potential kitty might be better at the federal level but in many cases, Internal Revenue Service (IRS) has stronger fraud detection systems in place than some states. If IRS does a better job at catching the bad returns, the fraudulent activity might slow down (or never make it into the system).
Additionally, Social Security Numbers are checked and cross-checked at the federal level, making it more difficult to file more than one return with the same number. For state purposes, the same level of checks doesn’t exist – either inside a state or between states – so that a single Social Security Number could be filed at multiple agencies in potentially multiple states without any knowledge that the number was being used fraudulently.
Using online software makes the process potentially easier for fraudsters. As noted by many of my readers over the past couple of days, online tax software requires no actual verification of identity – you don’t have to scan your license or government ID to file a return. You also don’t have to provide a paper tax form, like a W-2, to a specific individual when you file online. You simply need a computer and an internet connection. The lack of controls online make it appealing to those looking to cheat.
That begs the question, then, why aren’t all online tax software companies seeing the same kinds of issues? It may have to do with security screens but it could be even more simple: pricing and order of acceptance.
Like many other tax software companies, TurboTax allows taxpayers to file for free. This is great for taxpayers – but also for fraudsters: they can cheat for free. In other words, there’s very little outlay required.
Order of acceptance may also be a factor. With a product like TurboTax, taxpayers can opt to print and mail a federal return, but electronically file the state return. If a fraudster wants to avoid detection, they can choose not to submit the federal return (which, remember, may have stronger controls) and instead, target states. If filing a federal return is required prior to or together with the state return, it could make it more difficult to cheat: the fraudster would have to jump through the federal screens before landing on the state screens. At least one competitor, H&R Block, does require federal e-file acceptance prior to transmitting the state e-file return.
This matter is far from resolved. While all of the major tax software companies are all open for business, all are acutely aware of the potential for fraud and have issued statements indicated that they are continually monitoring the situation during tax season. Additionally, state agencies are actively involved in reviewing taxpayer returns for suspicious activities. And, of course, IRS continues to warn taxpayers about the potential for identity theft and fraud.
This matter is far from resolved. While all of the major tax software companies are all open for business, all are acutely aware of the potential for fraud and have issued statements indicated that they are continually monitoring the situation during tax season. Additionally, state agencies are actively involved in reviewing taxpayer returns for suspicious activities. And, of course, IRS continues to warn taxpayers about the potential for identity theft and fraud.
If you have specific concerns, individual companies advise the following:
- HR Block. If you need help, contact Customer Support at
 1.800.HRBLOCK FREE (
1.800.HRBLOCK FREE ( 1.800.472.5625 FREE).
1.800.472.5625 FREE). - TaxACT. If you suspect you may be a victim of fraud, please contact TaxACT (
 319.373.4514) and your state agency immediately.
319.373.4514) and your state agency immediately. - TurboTax. To assist any customers who believe they are victims of tax fraud, Intuit has implemented a plan that includes a dedicated toll-free number,
 1.800.944.8596 FREE, with direct access to specially trained identity protection agents who will provide comprehensive support and filing assistance.
1.800.944.8596 FREE, with direct access to specially trained identity protection agents who will provide comprehensive support and filing assistance.
So, the story is: During the Turbotax filing process, the user is given the option to efile. The federal file is free, but it costs some amount (eg $19.99) to efile the state. In addition, the user is given the option to have the federal and/or the state refund to be directly deposited into the user's (checking) account. To use the direct deposit, the user has to provide the route and account number of the account where the refund should be deposited.
Here was where the problems started. To sign up for direct deposit, the user checks a box for direct deposit. Two things can happen. If the user has used Turbotax last year, the routing and account fields are filled in from the previous return; otherwise the user has to enter the routing and account number. The automatic fill in is certainly convenient, but it turns out that it can be incorrect. The user is supposed to verify the routing and account number, but, in this case, that didn't happen. It was assumed to be correct. The entered routing and account number were incorrect! In fact, as I will describe subsequently, it was to a route and account that was completely unfamiliar to the user.
In addition to direct deposit, Turbotax gives the option to deduct the cost of the state efile (again, something like $19.99) from the federal refund. Sounds good, huh. No fuss. Deducting the cost of the state efile is a bait and switch. It turns out that Turbotax charges $34.99 to do this. Don't blow through the forms and miss this! Furthermore, your remainder tax refund seems to take a different route from the IRS to your deposit account. A third party bank, The Citizens Banking Company, in Ohio, fronted by a third party company, Tax Products Group (TPG) in California, handles the transactions. Apparently, the tax refund is sent by the IRS and the state bank to TPG. TPG takes out the $34.99 and then sends the tax returns on to the route and account the user provided. (By the way, if you look at ALL the forms created by Turbotax as part of your return, if you have opted to have this done, you have created and agreed to a 4 page contract. Bet you didn't know that.)
In this case, the route and account entered by Turbotax had no relationship to my acquaintance. After many inquiries the net is: TPG says then received the IRS refund, processed it, and sent the money on to the route and account number. The route number was to Chase Bank in Illinois. But, it turns out that the account number is not recognized by Chase. Chase did not receive the money. It should have been rejected by Chase back to TPG. TPG has washed there hands of the whole thing- they sent a form "findings" letter saying Chase has the money. Turbotax has been giving a royal run around. The individuals I talk to each time I call seem very helpful, but nothing happens.
More to come... But the takeaway is to not do direct deposit through Turbotax, especially if you opt to take funds out of the federal refund to pay for the state efiling. Something is wrong with the process! Fraud? Faulty programming?
Here was where the problems started. To sign up for direct deposit, the user checks a box for direct deposit. Two things can happen. If the user has used Turbotax last year, the routing and account fields are filled in from the previous return; otherwise the user has to enter the routing and account number. The automatic fill in is certainly convenient, but it turns out that it can be incorrect. The user is supposed to verify the routing and account number, but, in this case, that didn't happen. It was assumed to be correct. The entered routing and account number were incorrect! In fact, as I will describe subsequently, it was to a route and account that was completely unfamiliar to the user.
In addition to direct deposit, Turbotax gives the option to deduct the cost of the state efile (again, something like $19.99) from the federal refund. Sounds good, huh. No fuss. Deducting the cost of the state efile is a bait and switch. It turns out that Turbotax charges $34.99 to do this. Don't blow through the forms and miss this! Furthermore, your remainder tax refund seems to take a different route from the IRS to your deposit account. A third party bank, The Citizens Banking Company, in Ohio, fronted by a third party company, Tax Products Group (TPG) in California, handles the transactions. Apparently, the tax refund is sent by the IRS and the state bank to TPG. TPG takes out the $34.99 and then sends the tax returns on to the route and account the user provided. (By the way, if you look at ALL the forms created by Turbotax as part of your return, if you have opted to have this done, you have created and agreed to a 4 page contract. Bet you didn't know that.)
In this case, the route and account entered by Turbotax had no relationship to my acquaintance. After many inquiries the net is: TPG says then received the IRS refund, processed it, and sent the money on to the route and account number. The route number was to Chase Bank in Illinois. But, it turns out that the account number is not recognized by Chase. Chase did not receive the money. It should have been rejected by Chase back to TPG. TPG has washed there hands of the whole thing- they sent a form "findings" letter saying Chase has the money. Turbotax has been giving a royal run around. The individuals I talk to each time I call seem very helpful, but nothing happens.
More to come... But the takeaway is to not do direct deposit through Turbotax, especially if you opt to take funds out of the federal refund to pay for the state efiling. Something is wrong with the process! Fraud? Faulty programming?
Monday, March 16, 2015
Interesting Web Site: Health Indicators By County
The CDC has a web site that provides a comparison of CDC health indicators between your county and a "peer group" of counties similar (by their standards) to your county. It can be informative, with a grain of salt (but not too much; too much salt is unhealthy.). The web site URL is http://www.cdc.gov/communityhealth Note that when I entered that into the address bar, my browser search or maybe the website itself rerouted me to http://www.cdc.gov/nccdphp/dch/. At that point it is difficult to find the right link on the page. So, instead, I did a search on CHSI:
That got me to the right web page.
Community Health Status Indicators - CHSI
That got me to the right web page.
Friday, March 13, 2015
Wow! Did you see the number of Microsoft updates this week?
This week's updates seems like an all time record for number of updates. On my 8.1 Windows computer I had this:
Why? I update at least once a week (Tuesday). Here is a discussion of this unusual event from C/Net.
Why? I update at least once a week (Tuesday). Here is a discussion of this unusual event from C/Net.
Sunday, March 8, 2015
Problem: Internet Explorer crashes, and keeps crashing and crashing... This is an AVG Problem Too
I saw the above problem today. Like the Google case (previous blog entry), the subject symptom is caused by AVG Safeguard Toolbar. Remove it using your version of Windows program uninstall program.
Saturday, March 7, 2015
2015 Problem: Google Chrome error "Your profile could not be opened correctly" and how to Fix
Ignoring the fingernails on the blackboard feeling of that "correctly" dangling participle, Google Chrome recently started throwing an error when started:
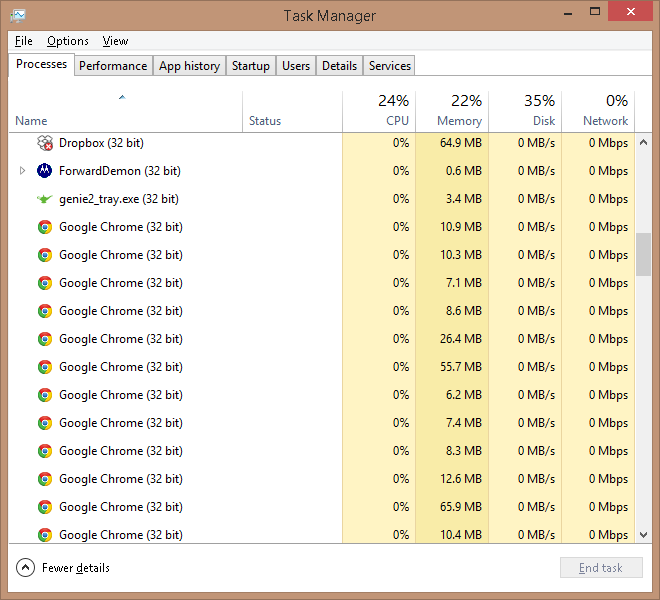
Yes, this was after I had closed Google Chrome. Those other processes support various Google functions.
After searching the web and trying different solutions, here is the one that worked for me. I found the solution on the AVG support site. https://support.avg.com/SupportArticleView?l=en_US&urlname=Google-Chrome-error-Your-preferences-can-not-be-read-or-Your-profile-could-not-be-opened-correctly. Evidently, a recent update contains a bug that causes this Google Chrome error. AVG knows about it but hasn't fixed it, so their solution is to remove the Google Chrome (and other browsers) addon called AVG Safeguard; remove as in uninstall.
I can't just stop this entry here, because it turns out that the removal is trickier than the directions describe. Here is how to do it.
- Exit Chrome and any other browsers you have open.
- If you use any Google applications, such as drive, Google+ Photos, etc, this does not close all running instances of Google Chrome. Open Task Manager (Ctrl-Alt-Del) and show the Processes tab (and leave it open to watch what is happening to the Google Chrome instances). I found this:

Yes, this was after I had closed Google Chrome. Those other processes support various Google functions.
- If you have the autosync feature running (the colorful pinwheel), right click on that icon in the notification area and "Exit."
- If you have Google Drive running (the colorful triangle), right click on the Google Drive icon in the notification area.
Click on the three dots in the upper right corner and then click on "Quit Google Drive". At this point you may or may not have removed all the Google Chrome instances and some of the supporting processes, such as Google Drive. If there are any left, right click on the Google Chrome instance and click "End task." Your computer should still be stable. If it isn't, then something else is going on.
Now, if you wish, close Task Manager.
Go to Control Panel.Default Programs.Programs and Features. Let all the programs fill in. Find the entry "AVG SafeGuard Toolbar" and click on it. Click the "Uninstall" word at the top of the list. The removal process should start.
Let it go through to completion. When you close the uninstall window, AVG might throw up a browser page asking about your experience. Tell them the toolbar blew away Google Chrome and so the toolbar sucks. By the way, if your default browser is chrome, well, it is all fixed!
At this point, you might want to restart your computer to restart all the processes you stopped.
It looks like this error started with AVG 2015, but can't be sure if it was an update to that version or was in that release. I think the former because this started happening to me on 5Mar2015.
Thursday, March 5, 2015
New Bug for Safari and Android browser... and a test to see if you are affected.
From a ZDNet article:
"The FREAK bug disclosed yesterday is the latest in a series of vulnerabilities affecting the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols used to encrypt traffic between an HTTPS website and a browser.
A man-in-the-middle attacker can force connections between affected browsers and websites to downgrade from 'strong' RSA encryption to a weaker version known as 'export grade' RSA. That weaker version is a by-product of laws from the 1990s that made it illegal to export from the US products with strong cryptography."
The gobbledygook goes on. The point is the defect was inserted in the code to comply with NSA requirements after 9/11. It impacts some Safari and some Android browsers.. Android will be patched before Safari. To see if you are impacted, run this: FREAKattack.com's client checker . Note that this actually runs the check and gives you the result. It is not a scam.
How to learn about new features and new applications offered by Microsoft
I found a great site for learning the features of the latest Microsoft applications (eg, Office) updates are and what the future offerings will contain. It is http://blogs.office.com/ . Check it out. You might want to bookmark it and visit it once in a while.
Subscribe to:
Posts (Atom)




